

Is this eduroam?


Is this eduroam?
To me, Endless OS seems to be the best fit for you; install it once and you never ever have to give it a second glance for troubleshooting or whatsoever. It achieves this through using “a read-only root file system managed by OSTree with apps installed using Flatpak.”. This translates to:


filesystem based encryption is really cool.
Can’t agree more.
Sorry to be that guy, but you should just sit down and go over Qubes OS’ documentation. Some specific entries that might prove useful:
If you ask me, read a lot more beyond these. But if you really got no time, then at least suffice with the aforementioned.
Wish ya good luck!


Mandatory read on the subject for the curious (also goes over Secure Boot, Boot Guard etc):


Are you referring to Qubes OS? If so, what do you mean exactly with hardware support?


IIRC, it stops working whenever you disable JavaScript.
I think we’ve probably already spoken on the matter.
That’s definitely possible. Unfortunately, I don’t recall it 😅.
Indeed, Lemmy has a serious dearth of users interested and using secure distros over the averages.
It’s definitely better at this than the platform that starts with an “R” and rhymes with “shit”.
Thanks for your efforts; I do not know how to follow users on Lemmy but if I did I’d follow you. Do you have a blog/any other forum you’re more active on?
That’s such a compliment. This is definitely one of the nicest things I’ve read on Lemmy. I really appreciate it.
Unfortunately, I’m only somewhat active on Lemmy. FWIW, consider checking out the following places if you haven’t yet:
And, of course, Qubes OS’ forums.
Personally, I find it difficult to justify the time to learn Secureblue (especially the immutable part) or NixOS on Qubes because custom DispVMs with curated salt states work so well already. I’m interested in use-cases that will improve my security but I haven’t found any dialogue on this yet. If you do have opinions on this and know where I can look, I would greatly appreciate it!
As I’ve previously alluded to, I don’t have any hands-on experience with Qubes OS yet. So, I don’t think I can contribute meaningfully in this discussion. However, IIRC, there are some discussions found on the forums/discussions page for Qubes OS.
Aight. I’m glad to hear that that has been resolved. I’d love to hear about your experiences on secureblue, so consider to report back. Finally, note that as a hardened distro, some things might work differently from what you’d expect. So be prepared to relearn a thing or two 😉.
Currently I got no time to go over this in more length. So apologies*. However, I still want to offer/provide a brief and concise answer. I will (hopefully tomorrow) return at this in more length.
Now i already setup my container & install some packages in it but the shortcut is missing from application launcher (a.k.a start menu), how i can link the shortcut from package inside toolbox to host application launcher ?
Short answer is that Toolbx for a long time (and perhaps still) didn’t really support this feature. Sure, you could make it work, but it was a bit hacky. If this is a concern of yours, consider switching over to Distrobox. With distrobox, it’s as easy as (while inside the container) distrobox-export --app <name app>. I will return at this tomorrow with the Toolbx way to do the same. I will also explore how Distrobox fares compared to Toolbx etc.
If i made a file (ex text file) from inside container will it show in Home directory ?
Yes if you’ve saved it in the Home directory to begin with.
If something crashed inside container will it also crashed my host system ?
Nope.
Why some packages doesn’t work inside container like Wine, Lutris, or Bottles ?
Interesting. I don’t recall ever experiencing problems with either Wine or Lutris inside a Toolbx/Distrobox container. I’m also confident that Bottles should work.
Does it’s need special dependencies to make it work ?
This is definitely something that might be at play. Consider reporting the terminal output whenever you try to work with Wine, Lutris and Bottles.
Furthermore, expect some containerized solutions tomorrow for these 😉.
Can packages that modifying system (ex green tunnel, vmware, or QEMU, & hblock ) work fine ?
I’m not familiar with all of them. Though, you may expect troubles. I do recall I had to resort to rpm-ostree in order to make QEMU work. However, it’s a fast moving space, so I wouldn’t be surprised if Toolbx/Distrobox-based solutions exist for this. For example, since relatively recently, it has been possible to have a functioning Waydroid within Distrobox. I will also more exhaustively go over this matter tomorrow.
Aight, so you didn’t like my methodology. That’s fine; I’ve got no qualms with putting in the work. So, if you allow me, I would like to propose the following:
flatpak install org.gnome.Boxes*.Whonix is an OS exclusively meant to be used within a VM; at least, until Whonix-Host is released. Therefore, I didn’t include it as it’s not actually competing within the same space; as it can be run on any of the aforementioned systems within a VM. Finally, it’s worth noting that by its own documentation, it’s desirable to do so with Qubes OS.
Please allow me to link to an earlier comment of mine that goes over this in more length. You may also find it copied-and-pasted down below:
First of all, apologies for delaying this answer.
Disclaimer:
Qubes OS >> secureblue >~ Kicksecure
Context: Answering this question puts me in a genuinely conflicted position 😅. I have immense respect for the Kicksecure project, its maintainers and/or developers. Their contributions have been invaluable, inspiring many others to pursue similar goals. Unsurprisingly, some of their work is also found in secureblue. So, to me, it feels unappreciative and/or ungrateful to criticize them beyond what I’ve already done. However, I will honor your request for the sake of providing a comprehensive and balanced perspective on the project’s current state and potential areas for improvement.
Considerations: It’s important to approach this critique with nuance. Kicksecure has been around for over a decade, and their initial decisions likely made the most sense when they started. However, the Linux ecosystem has changed dramatically over the last few years, causing some of their choices to age less gracefully. Unfortunately, like most similar projects, there’s insufficient manpower to retroactively redo some of their earlier work. Consequently, many current decisions might be made for pragmatic rather than idealistic reasons. Note that the criticisms raised below lean more towards the idealistic side. If resources allowed, I wouldn’t be surprised if the team would love to address these issues. Finally, it’s worth noting that the project has sound justifications for their decisions. It’s simply not all black and white.
With that out of the way, here’s my additional criticism along with comparisons to Qubes OS and secureblue:
What are the main advantages of using this, that make it more secure?
More secure compared to your average distro? Or more secure compared to a specific set of distros? Unless, this is properly specified, this comment could become very unwieldy 😅.
Thanks in advance for specifying!
I daily drive secureblue; or, to be more precise, its bluefin-main-userns-hardened image.
“Why?”, you ask. Because security is my number one priority.
I dismiss other often mentioned hardened systems for the following reasons:
Maybe they’ve fixed it by now but at the time of my comment the page led to the mentioned empty standard folder path you’d expect on a regular installation.
Alright, so through the flathub remote-info --log flathub org.mozilla.firefox command, we can view which commit was active at that moment.
Command yields:
Firefox - Fast, Private & Safe Web Browser
ID: org.mozilla.firefox
Ref: app/org.mozilla.firefox/x86_64/stable
Arch: x86_64
Branch: stable
Version: 129.0
License: MPL-2.0
Collection: org.flathub.Stable
Download: 98.6 MB
Installed: 259.6 MB
Runtime: org.freedesktop.Platform/x86_64/23.08
Sdk: org.freedesktop.Sdk/x86_64/23.08
Commit: 57fc35d29f0ee4915ebd903e2b9ce5497972c175cf0a6950153ec91d6f1b3e33
Parent: 6a16f6a509340ad3bb833c9d9aa794ed78910aa43803a7420438b880aa0a6ce0
Subject: Export org.mozilla.firefox
Date: 2024-08-06 12:45:05 +0000
History:
Commit: 6a16f6a509340ad3bb833c9d9aa794ed78910aa43803a7420438b880aa0a6ce0
Subject: Export org.mozilla.firefox
Date: 2024-07-26 13:29:41 +0000
Commit: 5b92a5aa533a8f68fe1d73f3910392018c4d4bb9f4370ee0577384e101999ce8
Subject: Export org.mozilla.firefox
Date: 2024-07-23 14:34:25 +0000
So, at the time of your comment, commit 6a16f6a509340ad3bb833c9d9aa794ed78910aa43803a7420438b880aa0a6ce0 was active and deployed on your system. Let’s find out what downgrading to this commit yields.
Downgrading through sudo flatpak update --commit=6a16f6a509340ad3bb833c9d9aa794ed78910aa43803a7420438b880aa0a6ce0 org.mozilla.firefox, after which the about:profiles page is opened on this downgraded Firefox yields:
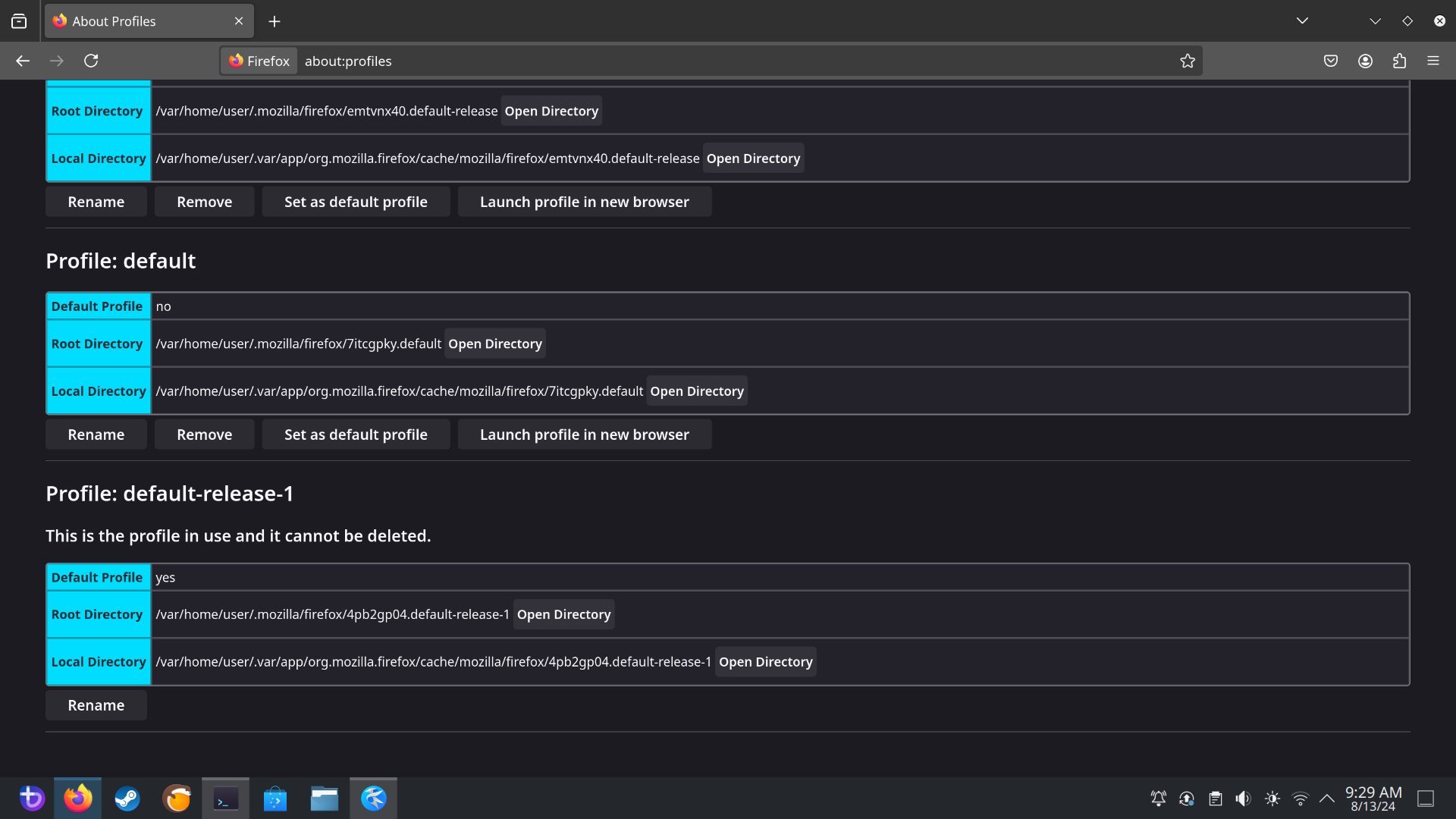
The beautiful part is that, as Flatpak is containerized anyways, anyone can downgrade to the earlier commit and it yields the exact same result. So, please feel free to verify this for yourself.
So, as a result, if the logic and the appliance is sound, then this showcases that your claim is either still true and portrays an anomaly -which I would deem as highly unlikely- or it’s simply false and you were just mistaken.
Finally, if I’ve messed up at any of the steps, then please feel free to correct me.
lol, the full answer I had written somehow was ripped to pieces. I’ll therefore keep it brief.
about:support while it’s found (as seen below) in about:profiles instead. I know it’s found in Firefox, I (just) messed up the exact spot. Therefore, thank you for countering misinformation!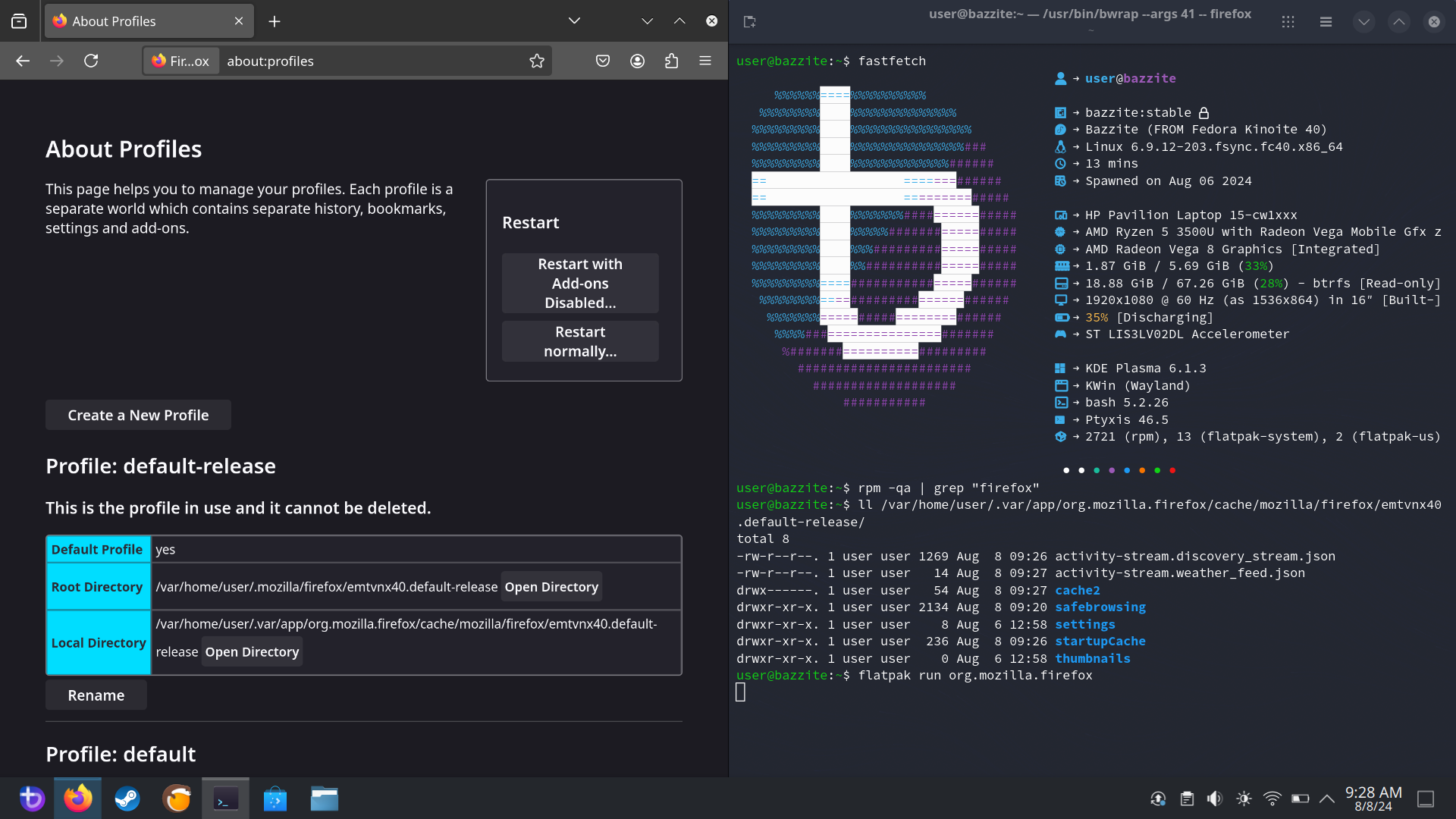
In a lot of educational institutions over the world, they truly on eduroam for their bidding. While it’s not perfect, it does offer a python script by which proper connection to the network is established. I guess it’s unfortunate to know that it’s not eduroam then, as I wouldn’t know what the solution would be.